Since Microsoft announced the RDP Shortpath feature was going to be enabled by default on September 6, 2022 for all Azure Virtual Desktop (AVD) customers, monitoring and troubleshooting this feature has become important. RDP Shortpath feature improves the AVD connectivity by establishing a direct UDP protocol between the AVD session hosts and the Remote Desktop Client by reducing the dependency on gateways. You will be charged for egress Internet traffic as per Azure standard pricing. Azure RDP Shortpath feature provides the following key benefits to users:
- Increases the Bandwidth available for each user session.
- Decreases the Round-Trip Time (RTT) and improves User Experience (UX) for latency sensitive applications and input methods.
- Allows you to configure Quality of Service (QOS) priority for RDP Shortpath connections by specifying a throttle rate.
- If the RDP Shortpath is not possible for the user connection, the connection automatically falls back to the TCP based reverse connect transport and uses Azure Gateway for the connectivity.
RDP Shortpath provides two configuration options:
- Managed networks – In this option, you need to configure Azure Network Security Group to allow inbound UDP port 3390 so that your endpoint can connect to the session host in the host pools. Due to security reasons, this option is meant for trusted connections established through Azure Express Route or Site-To-Site VPNs. More information can be found here.
- Public networks – In this option, no UDP port 3390 to the session host is required. So, Azure Express Route or Site-To-Site VPNs is also not required. More information can be found here. There are two connection types when using a public connection, which are listed here in order of preference:
- A direct UDP connection using the Simple Traversal Underneath NAT (STUN) protocol between a client and session host.
- An indirect UDP connection using the Traversal Using Relay NAT (TURN) protocol with a relay between a client and session host. This is in preview.
Currently, you can verify the RDP Shortpath feature by clicking the “Connection Information” in the blue bar as shown below. As you can see below, it says ‘UDP is enabled’ and the further down states UDP as the transport protocol.
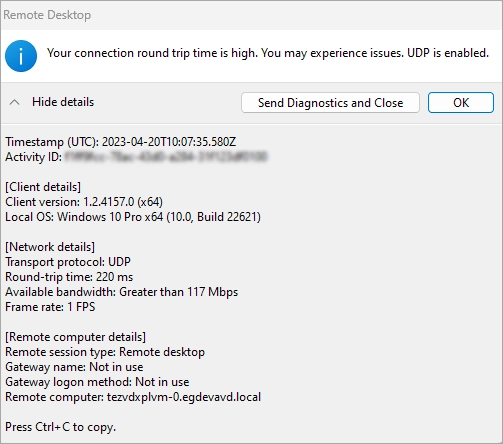
RDP Shortpath is enabled but not working
As discussed above if there is a problem with RDP Shortpath, it will automatically fallback to an alternative protocol. Rather than “Transport protocol: UDP” (as seen in Figure 1) you may see “Transport protocol: WebSocket”.
RDP Shortpath for public networks will work automatically without any additional configuration, providing networks and firewalls allow the traffic through and RDP transport settings in the Windows operating system for session hosts and clients are using their default values.
Microsoft Learn has a very good overview of examples of network configuration for RDP Shortpath. If RDP Shortpath is enabled but not actually working – it is very likely that somewhere in the network or firewall configuration the traffic is blocked forcing the fallback behaviour. The section “Example Scenarios” on this page – RDP Shortpath – Azure Virtual Desktop | Microsoft Learn, is a very good place to start. It is very important to understand the critical role STUN and TURN servers often play in RDP Shortpath enablement (Note: at the time of writing TURN support is only in preview in Azure and only in some regions).
Problems with STUN servers can impact RDP Shortpath and I’ll cover how eG Enterprise monitors those later in this article. Microsoft also provide a troubleshooting tool for RDP Shortpath avdnettest.exe and advice, Troubleshoot RDP Shortpath for public networks – Azure Virtual Desktop | Microsoft Learn. Detailed configuration and verification steps for RDP Shortpath are given in – Configure RDP Shortpath – Azure Virtual Desktop | Microsoft Learn.
What is STUN?
STUN is used to establish a direct UDP connection between a client and session host. To establish this connection, the client and session host must be able to connect to each other through a public IP address and negotiated port. However, most clients don’t know their own public IP address as they sit behind a Network Address Translation (NAT) gateway device. STUN is a protocol for the self-discovery of a public IP address from behind a NAT gateway device and the client to determine its own public-facing IP address.
Key Metrics and Information when Monitoring RDP Shortpath
If you are managing a larger AVD infrastructure, you need answers to the following key questions.
- How many of my users are using RDP Shortpath for AVD connectivity?
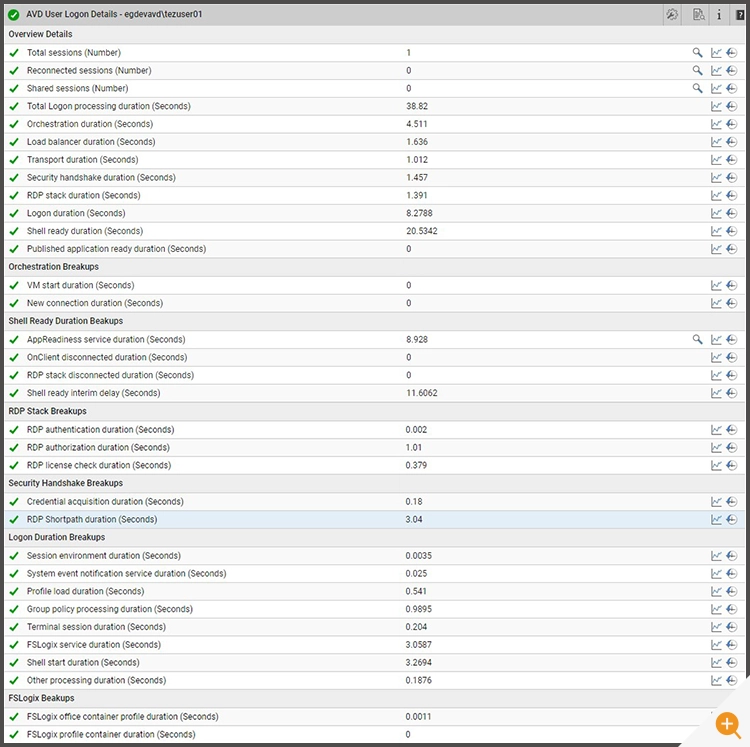
- Does RDP Shortpath affect the logon duration of the AVD user session?
- Who are using RDP Shortpath on managed network and where are they connected?
- Who are using RDP Shortpath on public internet and where are they connected?
- Is the RDP Shortpath listener is enabled and available on session host servers?
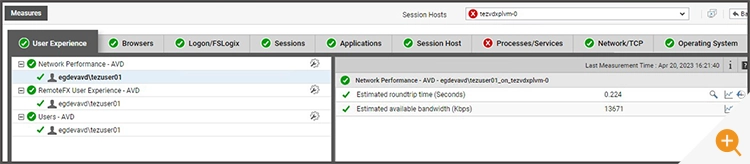
- What is the latency and bandwidth of the AVD user sessions?
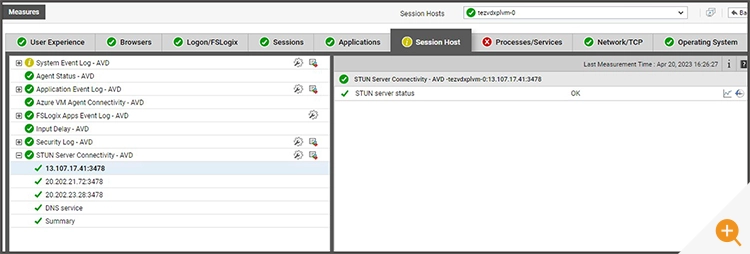
- Are STUN servers reachable from the session host servers?
Azure Virtual Desktop Insights does not provide any widgets in their workbook to answer the above questions when monitoring RDP Shortpath.
eG Enterprise AVD Monitoring answers the above questions and help you monitor the entire AVD infrastructure. We have some blogs that cover more information on how to setup and monitor and troubleshoot AVD infrastructure, please see: Azure Virtual Desktop Monitoring Technology | eG Innovations.
Accessing RDP Shortpath Metrics using eG Enterprise Monitoring
Out-of-the-box eG Enterprise will continually monitor and alert on problems in your AVD environments. Beyond this, session host monitoring is also performed on the AVD broker, where key connection data including that on Reverse Connect and RDP Shortpath connections is captured.
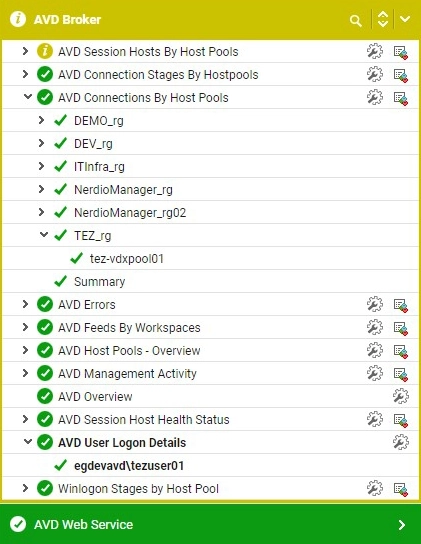
Next, in the captions of the next two figures, I’ll describe how to find out all the “Users using RDP Shortpath (UDP Connections)”.
In the AVD Broker monitoring layer, the “AVD User Logon Details” Test is a good way to access the impact RDP Shortpath is having on logon durations.
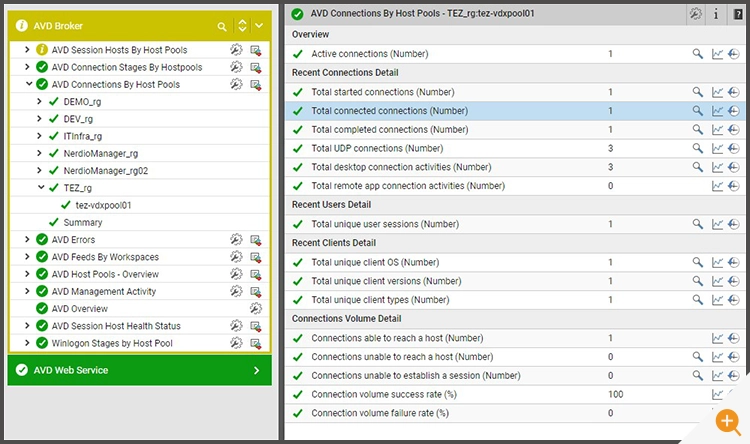
Administrators can also track and monitor the estimated latency and bandwidth of the AVD user sessions in eG Enterprise under the “Network Performance – AVD” test available in the AVD host pool component model. These metrics are collected from the AVD broker and presented for each user session in the appropriate AVD host pool.
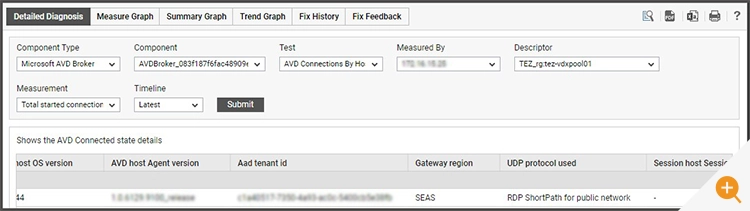
Are the STUN servers available?
Stun server availability is monitored continuously and can be viewed via the “Session Host” tab.
Please do feel free to check out my other blogs, see: Babu Sundaram, Author at eG Innovations, many of which are AVD related.
eG Enterprise is an Observability solution for Modern IT. Monitor digital workspaces,
web applications, SaaS services, cloud and containers from a single pane of glass.
eG Enterprise is an Observability solution for Modern IT. Monitor digital workspaces,
web applications, SaaS services, cloud and containers from a single pane of glass.
Related information:
- There are some great community blogs available, such as this one from Sune Thomson, see: Windows 365 End-User Experience – Part 1 – Mindcore Techblog.
- STUN plays a very similar role to Reverse Connect in AVD environments as a mechanism to access client IP information, for information on Reverse Connect see: Reverse Connect for Azure Virtual Desktops | eG Innovations.
- For information on monitoring and troubleshooting AVD, please see: Azure Virtual Desktop Monitoring Technology | eG Innovations
- For information on AVD Broker monitoring, alerting and troubleshooting, see: Monitor and investigate AVD Broker issues | eG Innovations.



 Babu is Head of Product Engineering at eG Innovations, having joined the company back in 2001 as one of our first software developers following undergraduate and masters degrees in Computer Science, he knows the product inside and out. Based within our Singapore R&D Management team, Babu has undertaken various roles in engineering and product management becoming a certified PMP along the way.
Babu is Head of Product Engineering at eG Innovations, having joined the company back in 2001 as one of our first software developers following undergraduate and masters degrees in Computer Science, he knows the product inside and out. Based within our Singapore R&D Management team, Babu has undertaken various roles in engineering and product management becoming a certified PMP along the way. 




