Introduction to Cisco NetFlow
Introduction to Cisco NetFlow
The increasing complexity of IT Infrastructure demands extensive network visibility and security. For those who have been working in networking for a while, NetFlow is not a new technology. Cisco created the network protocol “NetFlow” many years ago, which became the primary norm for collecting IP traffic information. Net Flow soon found its place within network management by providing valuable data of network performance and traffic analytics.
What is NetFlow?
NetFlow is widely used for collecting and analyzing network flow data statistics. This protocol’s datagram carries information like the source and destination ports, source IP addresses, destination IP addresses, IP protocol, and the IP service type. If we collect flow records from all flow-enabled network devices — routers, switches, etc. — we will have an understanding of where network traffic data is coming from and going to, how much traffic is being generated, who is consuming most bandwidth, and more. These data points can be used for anomaly detection, monitoring bandwidth usage, capacity planning, and to validate the effectiveness of QoS policy.
History of NetFlow and Versions Released Over Time
The first NetFlow version 1 was supported in all the initial flow monitoring releases. Versions 2, 3, and 4 were only usable as internal releases. v5 is the most commonly used version because it has a fixed packet format and is still supported by various routers. Versions 7 and 8 had a few improvements and they are no longer in practice. Meanwhile, version 9 is simplified since this version has FNF capabilities enabled and incorporates a dynamic packet format. Nine versions later, NetFlow still gains popularity not only due to its performance in network management, but also as a significant component of security operations.
IPFIX is referred to as NetFlow v10. It’s an industry-regulated version of the Cisco flow protocol.
The primary output of all these protocol versions is a flow record. This technology has matured over the years and created numerous formats of flow records. The most used flow-record format is version 9, which is a flexible way to record network performance data. It is the foundation of a new IETF standard.
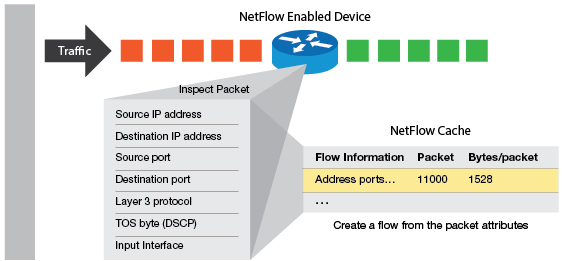
Understanding a NetFlow flow record
v9 comes with the Flexible NetFlow packets (FNF), which gives a broader view of what is happening in the network, thereby making it useful for:
- Network monitoring
- Application and user profiling
- Capacity planning
- Identifying security anomalies
- Network data mining
- Network fault troubleshooting
Why Use NetFlow: Key Applications
Optimizing Bandwidth Utilization and Capacity Planning
 NetFlow data allows network administrators to view the complete report on the traffic by specific interfaces in the network, specific protocols, and specific applications, which allows them to understand where bandwidth is getting consumed. By identifying the top talkers on the network, network admins can also see who the top consumers of bandwidth are, validate if that is relevant traffic, plan to optimize usage, and help in capacity planning. When using cloud applications, such as Office 365, Internet usage is likely to go up in organizations. Analysis of network traffic will let network admins know which application access has contributed to increased bandwidth, so they can understand the impact of Office 365 and such cloud applications on network bandwidth.
NetFlow data allows network administrators to view the complete report on the traffic by specific interfaces in the network, specific protocols, and specific applications, which allows them to understand where bandwidth is getting consumed. By identifying the top talkers on the network, network admins can also see who the top consumers of bandwidth are, validate if that is relevant traffic, plan to optimize usage, and help in capacity planning. When using cloud applications, such as Office 365, Internet usage is likely to go up in organizations. Analysis of network traffic will let network admins know which application access has contributed to increased bandwidth, so they can understand the impact of Office 365 and such cloud applications on network bandwidth.
Enhanced Network Visibility
 NetFlow provides complete visibility into the networks. You can specify the traffic sections you would like to monitor based on the tracks provided by flow data. For instance, you can classify Internet HTTP/S traffic by ports used or separate traffic by the protocol used. This gives network admins the ability to view the bandwidth usage (source and destination of traffic). Also, network admin teams can customize the data according to their need, be it for recording, detailed analysis or proper planning.
NetFlow provides complete visibility into the networks. You can specify the traffic sections you would like to monitor based on the tracks provided by flow data. For instance, you can classify Internet HTTP/S traffic by ports used or separate traffic by the protocol used. This gives network admins the ability to view the bandwidth usage (source and destination of traffic). Also, network admin teams can customize the data according to their need, be it for recording, detailed analysis or proper planning.
From the NetFlow data, network admins can correlate IP addresses with users who accessed them. Using this data, they can quickly predict QoS and allocate resources per user. And they can also prevent exposure of the network to a risk of malware and compromise, thereby getting a clear view of which user communicated with which IP address, which application the user accessed, and so on.
Enabling Root Cause Diagnosis
 NetFlow monitoring facilitates root cause analytics. When a user complains that email is slow, it could be because of a variety of reasons — a problem in the mail server, capacity problem with the user’s mailbox, or even a problem in dropped packets over the wire. By analyzing NetFlow flow records, network admins can understand the impact of email over the network and see if there are any packet drops or response time issues causing emails or any application access to be slow. This helps with root cause analytics and determining if the network was the cause of application performance slowdown.
NetFlow monitoring facilitates root cause analytics. When a user complains that email is slow, it could be because of a variety of reasons — a problem in the mail server, capacity problem with the user’s mailbox, or even a problem in dropped packets over the wire. By analyzing NetFlow flow records, network admins can understand the impact of email over the network and see if there are any packet drops or response time issues causing emails or any application access to be slow. This helps with root cause analytics and determining if the network was the cause of application performance slowdown.
Security Awareness
 Network security is another key application of NetFlow. By monitoring flow data, it’s simple to understand where most of your resources are being used. Various security attacks consume resources, so if any spikes occur in a particular time or location, they can be identified and investigated for a security breach. With advanced NetFlow analysis, these issues can be monitored, recorded, and improved.
Network security is another key application of NetFlow. By monitoring flow data, it’s simple to understand where most of your resources are being used. Various security attacks consume resources, so if any spikes occur in a particular time or location, they can be identified and investigated for a security breach. With advanced NetFlow analysis, these issues can be monitored, recorded, and improved.
How to Collect NetFlow Data
Typically network administration teams employ NetFlow monitoring tools for flow data collection and analysis. A NetFlow monitoring tool uses a flow collector to gather network packets and export the flow data from flow-enabled devices. A NetFlow analyzer is then used to process the raw flow data into meaningful insights through visualizations, real-time alerts, and historical reports.
Monitoring NetFlow requires three components:
- Flow exporter: a network device (a router or firewall) in charge of obtaining flow data and exports it to a flow collector
- Flow collector: a device that collects the exported flow data
- Flow analyzer: an application that examines and analyses the flow data collected by the flow collector
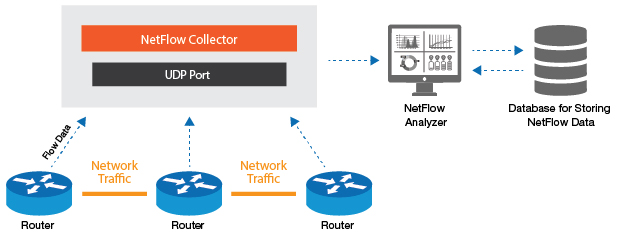
How a NetFlow monitoring tool collects and analyzes flow records
Insights Gained from NetFlow
 A NetFlow analyzer obtains different compositions of data from the incoming flow data. You can gain insights such as:
A NetFlow analyzer obtains different compositions of data from the incoming flow data. You can gain insights such as:
- Data about flow records across all the flow-monitored systems
- Traffic flows by specific protocol, application, domain, ports, Source, and destination IPs.
- Top conversations, addresses, and independent systems
- Sources and destinations by geographical location
This flow data can help you find out
- Who is using forbidden applications?
- Who is using significant bandwidth and slowing down the network?
- What protocols are heavily used over the network?
- Which end points are attacks originating from?
How eG Enterprise Helps with NetFlow Monitoring
eG Enterprise is an end-to-end IT infrastructure and application performance monitoring solution. With built-in support to monitor a wide array of network devices, eG Enterprise provides monitoring of network availability, performance, configuration changes, and more. With a dedicated NetFlow collector and analyzer built in, eG Enterprise can tap into flow records and export and analyze them to gain insights into traffic analytics, bandwidth usage, network congestions, top talkers, anomalous traffic spikes, and more. Get a free trial of eG Enterprise to try NetFlow monitoring in your network. Simplify network troubleshooting with eG Enterprise.
eG Enterprise is an Observability solution for Modern IT. Monitor digital workspaces,
web applications, SaaS services, cloud and containers from a single pane of glass.