What is Azure AD (Active Directory)?
 If you have arrived at this page but need a quick refresher on what Azure Active Directory is and why it is different to Active Directory that you might have installed on-premises, you might like to first read this quick run-down – What is Azure Active Directory.
If you have arrived at this page but need a quick refresher on what Azure Active Directory is and why it is different to Active Directory that you might have installed on-premises, you might like to first read this quick run-down – What is Azure Active Directory.
Why should you monitor Azure Active Directory?
I will not dwell too much on why you should monitor Azure Active Directory, but here are the top three reasons why we think everyone should be monitoring this service:
- Security – actively monitoring sign-in logs enables you to detect malicious attacks such as brute force penetration attacks as they happen. Spikes or anomalous patterns in the logs could indicate that your Azure AD is under attack. Proactive auditing of users and permissions to remove unnecessary access or dormant user accounts will ensure that the attack surface of your organization is minimized.
- Compliance – the auditing features built to eG Enterprise are designed to ensure traceability is enforced by process. Audit reports will help you demonstrate compliance to regulatory standards required in many industry sectors. Not only do you need to know who is accessing your cloud resources and from where, but you may need to demonstrate that you collect this information and retain it beyond the (often short) default retention timescales of Azure logging.
- End-user experience – Proactively monitoring Azure AD and components such as Azure Connect (connects Active Directory to Azure AD) can avoid users having issues logging in by detecting synchronisation issues. Monitoring certificate and secret expiration dates can ensure users do not experience issues with expired resources.
Which Azure Active Directory monitoring tool to use?
Unlike Active Directory, the younger Azure Active Directory is currently not supported by a wide range of monitoring tools. Two options that you have are:
- Azure Monitor – Azure Monitor is a service that provides a single pane of glass for monitoring all your Azure resources. It enables you to collect data from multiple sources, including Azure Resource Manager, Azure Services, and on-premises resources, and to visualize that data in a unified way. Azure Monitor also provides built-in alerts and actions that allow you to take automated corrective actions when issues are detected.
- Third-party monitoring tools such as eG Enterprise, an end-to-end monitoring platform that monitors every layer and every tier of applications running on Cloud and On-Premises Infrastructure. It can detect, diagnose, and resolves application performance issues before end-users are affected.
Both options have pros and cons, which we will discuss in the next section.
Monitoring Azure Active Directory with Azure Monitor
Azure Monitor is Azure’s native monitoring solution, just like CloudWatch is the native monitoring solution for AWS (Amazon Web Service). It is quick and easy to get set up and provision yourself, but it can get increasingly complex and costly.
Microsoft has extensive documentation on how to get started.
Advantages of Azure Monitor to Monitor Azure Active Directory
- Native tool available within Azure Subscriptions.
- Simple GUI is suitable for novices trying out Azure on a small scale.
- Good comprehensive documentation and a large amount of community self-support help available such as “get started” blogs and “how to” videos.
Disadvantages of Azure Monitoring
- All thresholds, metrics and alerts have to be manually configured or a significant investment made in bespoke scripting and tooling to automate.
- Only provides visibility and insights into the Azure tiers, so if problems occur outside of Azure, you need additional monitoring tools to give you coverage. Azure AD is widely used with on-premises or legacy Active Directory systems via Azure AD Connect. This introduces a layer of complexity as your IT team will have to manually switch and correlate between what Azure Monitor is telling you and what your third-party monitoring tool is saying.
- You are charged per alert for metrics monitored which means your monthly bill might escalate, or your finance team might ask you to reduce your monitoring costs so you have to make do with less visibility because you cannot afford to monitor all the metrics you need. Azure Monitor relies on Azure Log Analytics for which there are associated storage charges.
Monitoring Azure Active Directory with a Third-Party Monitoring Tool
At the time of writing, there are very few third-party monitoring tools for Azure Active Directory available.
Advantages of Third-party Monitoring Tools for Azure Active Directory
- End-to-end monitoring provides visibility into your entire IT infrastructure, quickly diagnosing and pin-pointing root-causes of performance problems.
- Predictable costs. (We have covered how to estimate Azure Monitor costs in a previous article).
- Usually more cost-effective, especially if looking to retain data beyond Azure’s 7/30-day defaults.
- Out-of-the-box dashboards, reports and help desk tools. Tools with easy-to-use GUIs remove the need for scripting, trawling logs and KQL (Kusto Query Language) queries and can be used by L1/L2 help desk staff without AVD (Azure Virtual Desktop) domain-specific knowledge.
- Synthetic monitoring options available that can proactively test and baseline login workflows using robot users.
Disadvantages of Third-party Monitoring Tools
- YAMT (Yet Another Monitoring Tool) – Unless a tool is replacing another or adding significant value it adds to budgeting costs and there are overheads to manage, lifecycle, patch and audit the additional tool.
- Many third-party tools, especially open-source ones, require significant effort and skills to integrate them such as custom scripting or configuration.
- Many third-party tools, especially open-source and free ones, come with no support contract or commitment compared to what is available with a Microsoft or Enterprise Vendor backed commercial solution. If something breaks then there might not be anybody to take a support ticket or they might not be obliged to help you or fix issues. The challenges of OSS (Open-Source Software) and freeware are discussed towards the end of this article.
5 things you need to monitor in Azure Active Directory
If the truth be told, there are actually hundreds of metrics, events, and log entries that you could be monitoring associated with Azure Active Directory. The more you can track, the quicker root-cause diagnosis is. However, if you are limited by budget because you are using Azure Monitor, then you will want to prioritize the metrics you do track. Indeed, domain intelligent AIOps (Artificial Intelligence for IT Operations) technologies such as eG Enterprise modify sampling criteria and prioritize certain metrics to reduce costs and ensure excessive noise of dumb Machine Learning algorithms is avoided.
Here are five areas that we think you should prioritize tracking. eG Enterprise does all of this for you out-of-the-box with no manual configuration and all the thresholds pre-set (both static and dynamic) so that you do not have to spend your time setting everything up.
1. Track and Monitor Users in Azure Active Directory
Managing Identity is a big challenge in a cloud environment, especially when users can potentially log in from anywhere. Additionally, users can often use different types of devices to log in and access cloud-hosted resources. Without a central Authentication and Authorization source, it is very difficult to manage who can login to what and who can do what with a cloud resource. On top of that, there can be thousands of identical identities from different organizations trying to consume cloud resources. Microsoft solves all the above challenges with the help of Azure Active Directory (Azure AD).
User accounts in Azure AD can grow quickly based on the business/organizational requirements. As Azure AD resides on the cloud, tenants are vulnerable to ransomware attacks, password spraying, brute force attacks, etc. Examples of recent Azure AD attacks and known security concerns include:
- How Azure AD Could Be Vulnerable to Brute-Force and DOS Attacks
- New Azure Active Directory password brute-forcing flaw has no fix
Ideally, an Azure administrator will need to find out (and better still, proactively monitor) the following from the Azure AD:
- How many users have been created in Azure AD?
- How many users are synced from On-Premises Active Directory and where were they synced and when did the last synchronization happen?
- How many users have weak passwords?
- How many users have a password with “is set not to expire” status?
- Are there any unlicensed users in the Azure tenant?
- Are there any disabled accounts in the Azure tenant?
- Are there any user accounts that are not part of any of the Azure AD Groups?
- Are there any stale user accounts in the Azure tenant?
- Have there been any malicious sign-in attempts?
- Have any risky sign-ins happened recently?
- Are any App registrations going to expire either in client secrets or SSL (Secure Socket Layer) certificates?
- What are the roles and permissions of App registrations?
- Have any brute force attacks happened recently for the tenant?
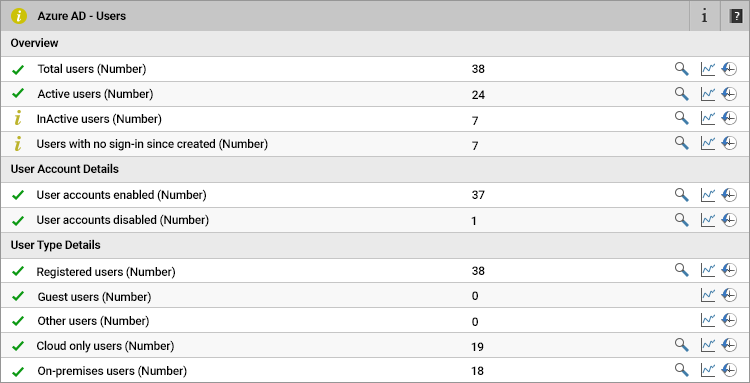
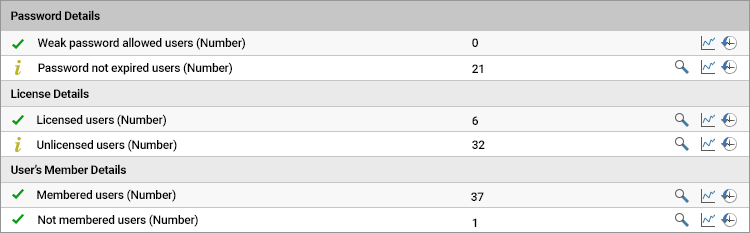
An in-depth guide on how to track and monitor Azure Active Directory users is available, see: Monitoring and Managing Azure Active Directory Users.
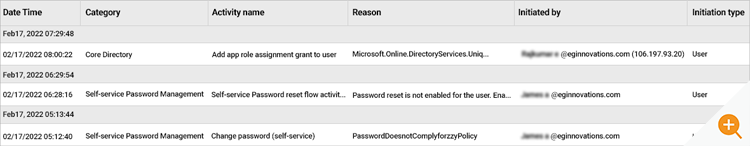
2. Monitor your Azure Active Directory Audit Log for Compliance and Security
As the Azure cloud administrator, you need to know who is accessing your cloud resources, how they are accessing it, what they are accessing, what changed when they accessed it and from where they accessed it, etc.
Azure AD (Azure Active Directory) provides answers to above by storing the information in two logs. The information stored in them is extremely valuable for troubleshooting, monitoring and for general security-related work, the logs are:
- Azure AD Audit log
- Azure AD Sign-in logs
The “Azure” Audit log provides you with access to the history of every task performed in your tenant. For example, information about changes applied to your tenant such as users and group management, and updates applied to your tenant’s resources, etc.
For a more detailed guide on how to monitor your Azure Active Directory audit logs for compliance and security, see: How to Ensure Compliance and Security by Monitoring Azure AD Audit logs.
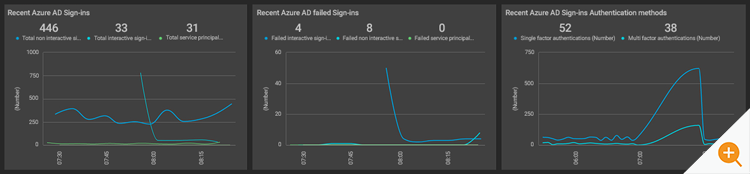
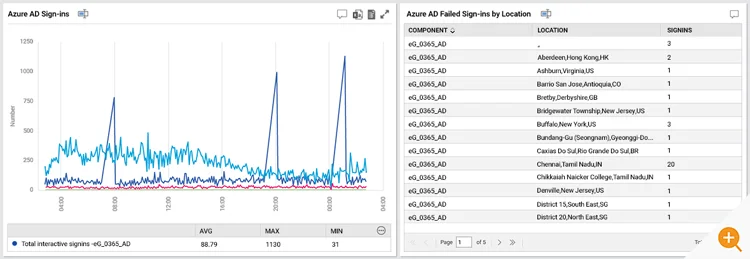
3. Sign-in Logs to Proactively Detect Attacks
Azure Sign-in log helps you to determine who has performed the tasks reported by the Azure Audit log. The Azure AD Sign-in log is an indispensable tool for troubleshooting and investigating security-related incidents in your tenant. Moreover, proactively, and constantly monitoring the sign-ins can prevent breaches, alert administrators to malicious attacks and anomalous usage patterns and enable them to reduce their vulnerability by ensuring systems are configured to allow access only to those users and services that need access using up-to-date best practice authentication mechanisms and so on.
To learn more about Azure compliance monitoring and detecting attacks by monitoring sign-in logs, check out this article, How to Monitor Azure AD Sign-ins logs and Detect Attacks Proactively.
4. Monitor Application Registrations and Track Client Secret and Certificate Expirations
The Azure Active Directory (Azure AD) is Microsoft’s cloud-based identity and access management (IAM) service and an identity provider (IdP). Azure AD is the backbone for authentication in Microsoft 365 and for thousands of cloud-based SaaS (Software as a Service) applications.
Azure AD provides several features for your organization and one of the features is the Microsoft Identity Platform. This feature helps developers to build applications where users and customers can sign into the application using their Microsoft identities or social accounts and get authorized access to application APIs (Application Programming Interfaces) or Microsoft APIs like “Microsoft Graph”.
You should register your application with Azure AD to prove your Identity and access resources in both Azure and Office 365 programmatically. Infrastructure as code (IaC) and DevOps Pipeline require an App registration in Azure AD for their automation.
Read our full guide on monitoring your Azure Active Directory Client Secret and certificate expirations – Monitoring and Alerting on Azure AD App Client Secret and Certificate Expirations.
5. Monitor Azure AD Connect if in Use
Azure AD Connect is the Microsoft tool designed to be a bridge solution between on-premises Active Directory and Azure AD. It enables IT admins to federate on-premises user identities to the Azure platform so that users can use the same credentials to access both on-premises applications and cloud services, such as Microsoft 365.
It is included for free with your Azure subscription. It offers multiple features, including synchronization, federation integration, and health monitoring. By default, the sync is one way: from on-premises AD to Azure AD. However, you can configure the writeback function to synchronize changes from Azure AD back to your on-premises AD. That way, for instance, if a user changes their password using the Azure AD self-service password management function, the password will be updated in the on-premises AD.
Synchronization errors and failures can lead to users having problems accessing resources and applications. eG Enterprise includes component monitoring for both Azure AD Connect and on-premises Active Directory.
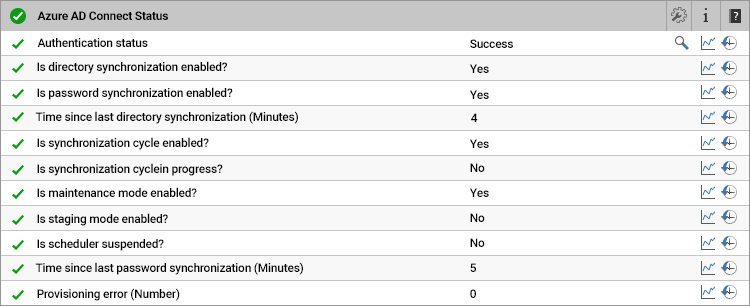
There are more details about how to monitor Azure AD Connector under the section “What is Azure AD Connector” within the article, What is Azure Active Directory.
This is just a quick guide on how to monitor Azure Active Directory. The next step for you is to follow through on this guide and either get started with Azure Monitor, or request a free 30-day trial of eG Enterprise.
With eG Enterprise you can be up and running in minutes thanks to the built-in metrics and thresholds!
Related Information
- A detailed overview of everything you need to know about Azure AD and interdependent components of an Azure deployment – What is Azure Active Directory
- Microsoft Documentation – What is Azure Active Directory? – Azure Active Directory | Microsoft Docs
- Using Azure AD in conjunction with Citrix technologies; currently in preview is Azure Active Directory Group-Based Support, read more: Citrix innovations to power your hybrid-cloud migration | Citrix Blogs
- Azure VMware Solution by CloudSimple – Use Azure AD as identity source on Private Cloud | Microsoft Docs
- Security can be improved by reducing the footprint of your deployments by identifying and rationalising unused resources and interfaces – often with the added benefit of Azure cost savings, see: Save Azure Cost by Finding Unused, Wasted and Orphaned Resources (eginnovations.com) and What is Azure Advisor? | eG Innovations
eG Enterprise is an Observability solution for Modern IT. Monitor digital workspaces,
web applications, SaaS services, cloud and containers from a single pane of glass.




 Babu is Head of Product Engineering at eG Innovations, having joined the company back in 2001 as one of our first software developers following undergraduate and masters degrees in Computer Science, he knows the product inside and out. Based within our Singapore R&D Management team, Babu has undertaken various roles in engineering and product management becoming a certified PMP along the way.
Babu is Head of Product Engineering at eG Innovations, having joined the company back in 2001 as one of our first software developers following undergraduate and masters degrees in Computer Science, he knows the product inside and out. Based within our Singapore R&D Management team, Babu has undertaken various roles in engineering and product management becoming a certified PMP along the way. 



