How to Ensure Compliance and Security by Monitoring Azure AD Audit logs
Azure Active Directory (Azure AD) is Microsoft’s multi-tenant, cloud-based Identity and Access Management (IAM) service. It takes care of authentication and authorization of user and application identities. It is the digital infrastructure that allows your employees to sign in and access external resources, such as those held in Microsoft 365 service, Azure Virtual Desktops (AVD), an ever-growing list of other SaaS (Software as a Service) applications, as well as those held on corporate networks. As such, Azure AD, how it is performing, how it is configured, and any changes made must be controlled, validated, and audited to ensure a secure and available infrastructure. Identifying and alerting on failed and timed-out activities.
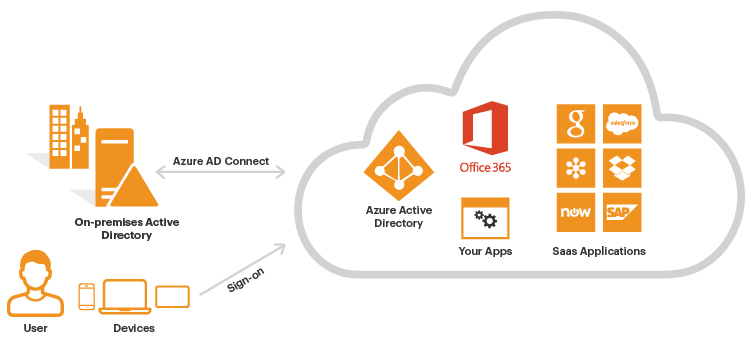
eG Enterprise monitoring for Azure AD leverages Azure AD Audit logs to allow administrators to:
- Receive proactive alerts and alarms if concerning changes are made and proactive notification if administration tasks fail or timeout to remediate immediately.
- Provide real-time and historical reporting for troubleshooting or audit purposes. Custom reports can be scheduled and archived to provide traceability and an audit trail for compliance and governance.
- Automate detailed diagnosis and capture of further information of failures to aid frontline help desk teams.
- Ensure audit data is available and archived long after Azure’s default 30-day retention period.
- Maintain visibility on Azure systems even when Azure may be down.
- Give non-domain experts full insight into the contents of Azure AD Audit logs out-of-the-box, no need to script or parse files, no need to know, write and maintain PowerShell or similar.
The Azure AD Audit log provides information about changes applied to your tenant. You can manually filter information or script queries to probe the changes in terms of the following categories in Audit log blade:
- User management
- Group management
- Application management
- Resource management
- Device management
- Role management
- Policy management and more categories available
With the help of the Audit log, you can answer the following questions:
- How many passwords were changed?
- How many users were changed?
- Were any federated domains were created?
- What licenses are assigned to a user or group?
- Has the owner change for the group?
- What applications are added or removed?
- Who gave consent to an application?
- What devices are added or removed?
The Audit log is accessible to the following roles:
- Security Administrator
- Security Reader
- Report Reader
- Global Reader
- Global Administrator
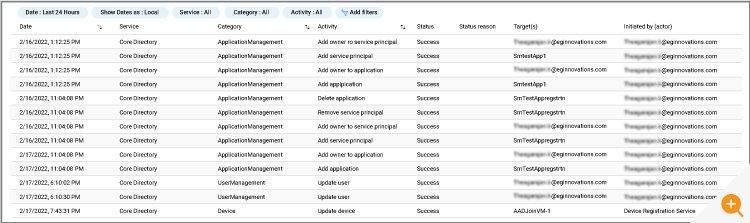
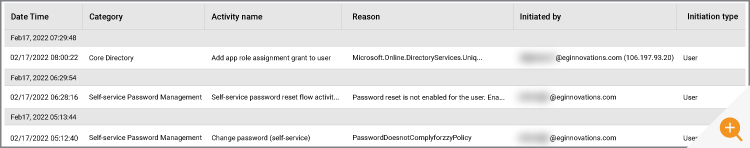
Audit log stores the information within Azure for 30 days by default for both P1 and P2 licenses and 7 days for free license SKUs. The Azure AD Audit logs allows you to query the information in the default view as shown below:
With the help of filters, you can query based on status, category, activity, service, etc. You can get the properties that changed/removed/added by clicking the individual records. If you want to store the above data for more than 30 days, you will need to explicitly store it into an Azure storage account and pay for the storage costs of retention. The Microsoft forums are full of users facing challenges with the default retention period and it is worth exploring some of these real-life cases to understand the scenarios in which administrators may be asked to retrieve data many months or years after security incidents have occurred; see:
- Sign-in logs older than the 30 day limit – Microsoft Q&A (A phishing scam, where the chargeback process requested information after several months.)
- I need Sign-in and/or audit logs from 2 years ago. Only have option for 7 days ago max. – Microsoft Q&A. (A legal case involving IP theft discovered long after the 7-day retention period.)
For administrators not being able to see who has logged in more than 30 days ago (or a mere 7 days on free SKUs) is a much debated challenge.
Additional challenges with the native Azure interface are that it is designed for passive reading and investigation. The administrator needs to read or scrape the logs to identify if events of interest have occurred and the unstructured nature of the records make it hard to obtain an overview of what has been changed or has failed.
How eG Enterprise monitors the Azure AD Audit logs?
eG Enterprise Azure AD monitoring monitors Audit log and proactively alerts upon audit failures. All audit log records are stored in the eG database. So, you can store this data for a longer period than the Azure default for security, compliance or troubleshooting reasons. eG Enterprise allows you to slice and dice this data without writing any KQL (Kusto Query Language) queries and without the need to import the workbooks from community repositories using custom reports and dashboards.
eG Enterprise’s Azure AD Audit log monitoring helps you to find answers for questions like:
- Have there been any failures in audit activities?
- Have any timeouts occurred during audit activities?
- How many successful audit activities happened recently?
- How many unknown audit activities?
The above metrics are categorized for User Management, Device management, Application management, etc., and populated to other categories as and when they are generated in Azure AD.
eG reports the following metrics for audit logs in a simple to understand interface:
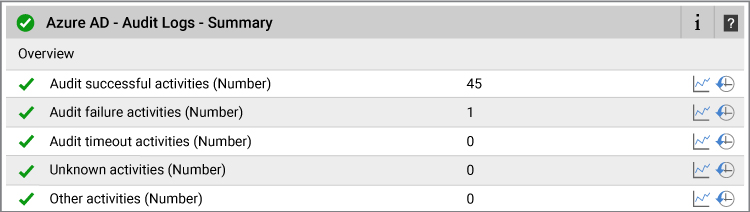
You can get the additional detailed view with eG detailed diagnosis. For example, the audit failure activities are shown below.
This blog post is the fourth in a series covering monitoring of various aspects of Azure AD, previously I have covered:
- An Overview of Azure Active Directory (Azure AD) – 101,
- How to monitor and audit Azure AD Users and
- Monitoring and Alerting on Azure AD App Client Secret and Certificate Expirations.
Monitoring and analytics reporting of Azure AD helps our customers comply with many compliance and regulatory standards such as PCI DSS, HIPAA, GLBA, FISMA, SOX, and more. Ensuring Azure AD is fully monitored helps our customers detect and respond to insider threat, privilege misuse, and other indicators of compromise, and improve their security processes.
Further Reading
Many of our customers also use eG Enterprise to monitor Azure infrastructures, other clouds, and on-premises infrastructure and applications. Please see the links below for relevant information:
eG Enterprise is an Observability solution for Modern IT. Monitor digital workspaces,
web applications, SaaS services, cloud and containers from a single pane of glass.




 Babu is Head of Product Engineering at eG Innovations, having joined the company back in 2001 as one of our first software developers following undergraduate and masters degrees in Computer Science, he knows the product inside and out. Based within our Singapore R&D Management team, Babu has undertaken various roles in engineering and product management becoming a certified PMP along the way.
Babu is Head of Product Engineering at eG Innovations, having joined the company back in 2001 as one of our first software developers following undergraduate and masters degrees in Computer Science, he knows the product inside and out. Based within our Singapore R&D Management team, Babu has undertaken various roles in engineering and product management becoming a certified PMP along the way. 




