How to Leverage Role-Based Access Control (RBAC) in eG Enterprise to Improve Security and IT Ops Efficiency
 eG Enterprise is a single pane of glass that provides monitoring and oversight of every layer and tier of your IT infrastructure. However, this does not mean every user in the organization has the same view of the IT infrastructure or needs to use the tool in the same way.
eG Enterprise is a single pane of glass that provides monitoring and oversight of every layer and tier of your IT infrastructure. However, this does not mean every user in the organization has the same view of the IT infrastructure or needs to use the tool in the same way.
In fact, controlling a user’s view of the monitored applications and infrastructure, as well as their privileges to perform tasks and access data via Role-Based Access Control, is a critical feature for our customers. This is important not only to ensure the product satisfies the needs of each user’s role (job) and responsibilities, but also to ensure security and data protection across the organization.
Role-Based Access Control (RBAC) in eG Enterprise not only allows you to give your employees the exact permissions they need to do their jobs, but it also enables administrators to limit those permissions to only those they need. Additionally, RBAC can be used to ensure their access to data and views of the infrastructure are restricted where appropriate.
This not only reduces the risks of rogue and ex-employees or contractors using insider knowledge to malicious ends but also enables clear delimitations and responsibilities to be divided between individuals and teams. eG Enterprise’s rich RBAC helps our customers satisfy many compliance and regulatory standards, such as PCI DSS, HIPAA, GLBA, FISMA, SOX, and more.
Our platform fully supports a rich suite of “Limited Component Access” controls associated with RBAC that allow customers to define zones, services, and segments based on factors, such as geographical location, functionality, or end-to-end service. RBAC alone allows permissions to be restricted but “Limited Component Access” allows granularity in what infrastructure those permissions are applied to.
What is RBAC?
 Within an organization, roles are created for various job functions. Permissions to perform certain operations are assigned to specific roles. Members of staff (or other system users) are assigned specific roles, and through those role assignments, acquire the permissions needed to perform particular system functions. Since the users are not assigned permissions directly, instead of acquiring them through their role (or roles), the management of individual user rights is a matter of assigning appropriate roles to the user’s account; this simplifies common operations, such as adding a user or changing a user’s department.
Within an organization, roles are created for various job functions. Permissions to perform certain operations are assigned to specific roles. Members of staff (or other system users) are assigned specific roles, and through those role assignments, acquire the permissions needed to perform particular system functions. Since the users are not assigned permissions directly, instead of acquiring them through their role (or roles), the management of individual user rights is a matter of assigning appropriate roles to the user’s account; this simplifies common operations, such as adding a user or changing a user’s department.
Sophisticated RBAC implementations may include functionality to define hierarchies of business units and/or user groups within organizations to securely segregate access and permissions further. The ability to define groups of users reflects Unix- and Windows-based permission systems better than simple role definitions.
RBAC in eG Enterprise: How it Helps?
The granularity of control eG Enterprise’s RBAC offers allows organizations to configure their monitoring and troubleshooting capabilities in numerous ways. Common customer choices we see include:
- Restricting Level 1 help desk staff to view only service/system health and alert information, but enabling second and third-level support engineers with greater insights into the health of each tier being monitored. The third level engineers may even get the ability to remotely interact with user sessions and even execute Remote Control commands and scripts within user sessions – e.g., to kill processes, logoff a user, or take a screenshot.
- In a large organization, there may be different domain experts (e.g., database admins, storage admins, network admins, etc.). These subject matter experts may only be interested in seeing the health of the components they are responsible for. RBAC enables the assignment of views for users that maps to the responsibilities they have in the organization. This ensures that your L1/L2 Citrix help desk staff do not have visibility or insight on your secure networking infrastructure, such as firewalls, switch failover architectures, and so on.
- MSPs (Managed Service Providers) who wish to allow tenants to self-service and manage their own help desk functionality within secure segregated view isolated from other tenants.
- Administrators and executives who wish to limit business information and overview reporting to senior management on a strictly need-to-know basis. Business-sensitive information, such as how much an organization is spending on Azure or AWS (Amazon Web Service), is controlled.
- Organizations who wish to define zones, services, and segments based on factors, such as geographical location, functionality, or end-to-end service, and allocate them to specific teams or staff. This way your IT team in Europe only sees alerts relevant to the infrastructure they manage.
- Those who have sensitive security infrastructure, such as firewalls and networking, and want them to be viewable only by vetted employees and on a need-to-know basis.
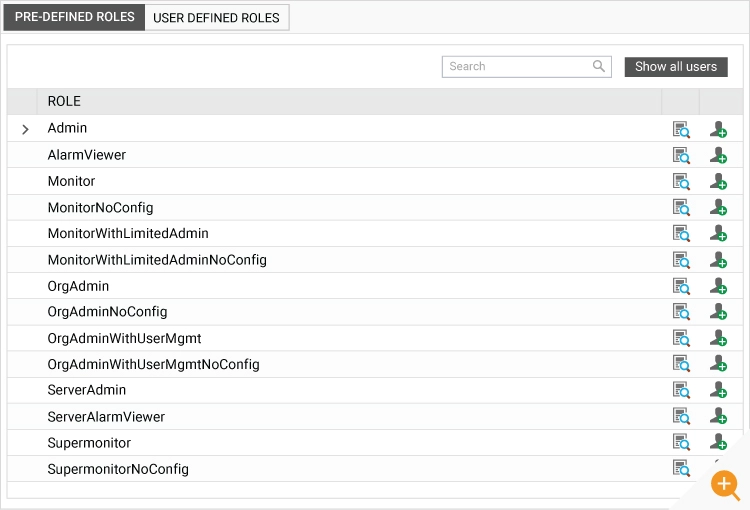
There are a large number of roles available by default in eG Enterprise that should suffice most users. (See the eG Enterprise documentation Adding New User Roles for more information.) Broadly, some of the built-in roles block access to specific tabs of the eG Enterprise console. Access to menus within each tab can also be controlled using these roles.
Custom Roles
For organizations with complex needs, eG Enterprise allows the definition of custom roles, “User Defined Roles.” Fine-granularity on permissions allows custom roles to be created for specific organizational roles. With these permissions, you can provide access to specific menus and features of the monitoring tool within any of the tabs of the user interface.
RBAC for Multi-tenancy Environments and MSPs
The release of eG Enterprise v7 saw the introduction of additional roles tailored to the needs of multi-tenant environments and MSP (Managed Service Provider) business models. eG Innovations offers a range of partner models to MSPs to enable them to grow their business by offering customers premium and additional services, such as a frontline help desk and enhanced monitoring and troubleshooting tools. The roles available to MSPs include the ability to delegate self-service capabilities to their tenants without compromising security; some information on these admin models is given in Multi-Tenant MSP Monitoring. You can also read more about how a selection of MSPs have grown their businesses using eG Enterprise Managed Services.
Controlling Access to Privileged Functionality
eG Enterprise contains a rich suite of Remote-Control Actions (RCAs) to assist the administrator with troubleshooting and issue resolution. These include the ability to shadow users’ sessions, terminate processes remotely, or change users’ GPOs (Group Policy objects). Many of these actions are powerful, and admins need to control access on a strictly need-to-use basis. As such, most organizations limit access in these instances.
Further, organizations can use RBAC to limit users’ abilities on a highly granular level. Beyond this, the use of Remote Control Actions is logged and can be audited for compliance and security purposes; organizations are able to trace and review the use of invasive and privileged activities, such as remoting into an individual’s desktop or changing the privilege of processes.
Personalized Views: Complementing RBAC
While RBAC determines what level of access a user has to the monitoring system, equally important is what portion of the monitored infrastructure can the user view and analyze. Personalized views in eG Enterprise determine the subset of the monitored infrastructure to which users have access. This subset can be configured by an administrator manually. Alternatively, this subset can be auto-determined.
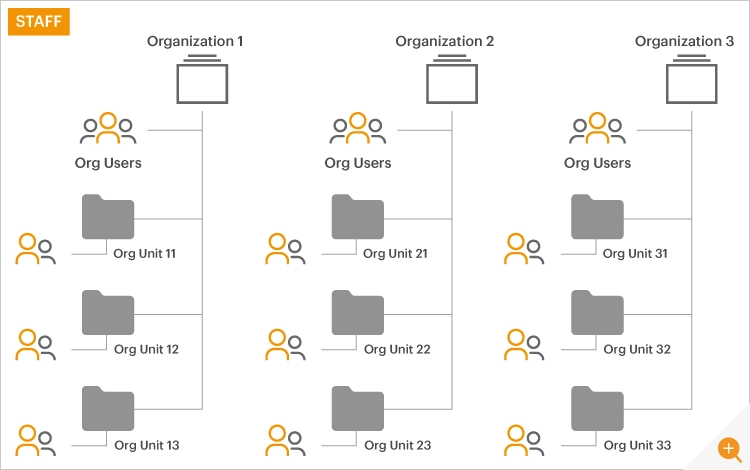
To assist with such auto-discovery, eG Enterprise supports three different entities:
-
Organization:
Typically in an enterprise deployment, there is only one organization. A SaaS/MSP deployment may have many organizations – one for each customer. Each organization has a strict delineation of responsibilities so there is no sharing of information across entities.
-
Organizational Unit:
Smaller user groups within an organization can be created as Organizational units – e.g., departments within an organization, support groups within a technical support cell, the different branches of an enterprise, etc. For example, the retail banking department and the call center can be different departments within a banking organization. An Organizational Unit can contain more organizational units or individual users.
-
User:
These are individual users who can belong to an Organization or an Organizational Unit.
Auto-mapping of components to organizations and organizational units is done using unique UUIDs assigned to each organization or OU. When a user of an OU downloads agents from the management server, these agents are auto-configured with the OU’s UUID. The UUID information is transmitted by the agents to the manager when they begin communication and this allows the infrastructure being monitored by these agents to be auto-assigned to users. This capability is particularly useful in SaaS deployments as it allows users to download and install agents, as well as auto manage these agents without needing any assistance from their MSP.
Sometimes, there may be a need to share access to a monitored infrastructure with others. For example, the database team may have multiple members, each of whom may need similar access. eG Enterprise’s three-level configuration of entities and assignment of UUIDs allows it to cater to such requirements as well.
Ensure the Rest of your Infrastructure Implements Best Practices for RBAC
 Most modern application stacks include their own RBAC implementations, and eG Enterprise can be used to monitor and audit that RBAC usage is compliant, appropriate, and secure, for example when accessing Microsoft Azure. Microsoft details Best practices for Azure RBAC well. eG Enterprise’s comprehensive monitoring for Azure Active Directory (Azure AD) will help you ensure you adhere to these best practices in a traceable and audited manner by process.
Most modern application stacks include their own RBAC implementations, and eG Enterprise can be used to monitor and audit that RBAC usage is compliant, appropriate, and secure, for example when accessing Microsoft Azure. Microsoft details Best practices for Azure RBAC well. eG Enterprise’s comprehensive monitoring for Azure Active Directory (Azure AD) will help you ensure you adhere to these best practices in a traceable and audited manner by process.
For those leveraging roles with high privileges, eG Enterprise includes the ability to allow for admin user access only from select locations (IP addresses), a fixed IP, or range of IPs usually associated with a privileged admin workstation.
Note: RBAC can be integrated with single sign on (SSO) using Active Directory Integration, SAML authentication, or 2FA support for high security.
eG Enterprise is an Observability solution for Modern IT. Monitor digital workspaces,
web applications, SaaS services, cloud and containers from a single pane of glass.
Learn More:
- Read more about monitoring Active Directory here: Active Directory Monitoring and Management.
- A recent series of blogs covers monitoring and auditing Azure AD Users and Accounts – see:
- Checkout our short how-to series of videos that covers how to configure users, as well as working with groups, services, zones, and segments to limit access and privileges within eG Enterprise; see How To Videos – YouTube.