Introduction
RSA Authentication Manager is a multi-factor authentication solution that verifies authentication requests and centrally administers authentication policies for enterprise networks. Use Authentication Manager to manage security tokens, users, multiple applications, agents, and resources across physical sites, and to help secure access to network and web-accessible applications, such as SSL-VPNs and web portals.
RSA Authentication Manager provides the following choices for strong authentication:
- RSA SecurID, which protects access using two-factor authentication with hardware and software-based tokens.
- On-demand authentication (ODA), which protects access using two-factor authentication by sending authentication credentials to users upon request through SMS text messaging or e-mail.
- Risk-based authentication (RBA), which protects access by assessing user behavior and matching the device being used to authenticate to assess the risk-level of an authentication attempt.
By leveraging devices that the user already owns, for example, a mobile phone, PC, or laptop, RBA and ODA enable multi-factor authentication with no tokens to manage. Figure 1 shows a deployment of the RSA Authentication Manager.
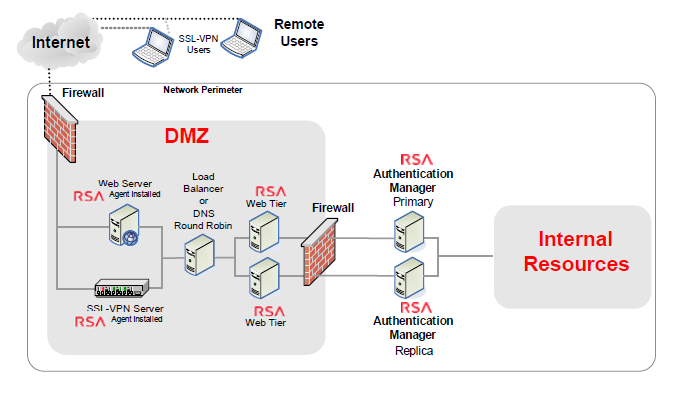
Figure 1 : The RSA Authentication Manager deployed in an environment
An RSA Authentication Manager deployment may have the following components:
-
Primary Instance: The primary instance is the initial Authentication Manager system that you deploy. The main functions of the primary instance include the following:
- Authenticating users.
- Enabling administration of Authentication Manager data stored in the internal database. You can perform tasks such as importing and assigning SecurID tokens, enabling risk-based authentication (RBA), adding LDAP identity sources, configuring self-service, generating replica packages, and generating agent configuration files and node secrets.
- Replicating changes due to administration and authentication activities.
- Hosting the primary RSA RADIUS server.
- Handling self-service requests.
- Maintaining the most up-to-date Authentication Manager database.
-
Replica Instance: A replica instance provides deployment-level redundancy of the primary instance. You can view, but not update, administrative data on a replica instance. A replica instance provides the following benefits:
- Real-time mirror of all user and system data
- Failover authentication if the primary instance becomes unresponsive
- Improved performance by load balancing authentication requests to multiple instances
- Ability to deploy a replica instance at a remote location
- Ability to recover administrative capabilities through replica promotion if the primary instance becomes unresponsive
-
Identity Sources: All users and user groups in your deployment are stored in identity sources. RSA Authentication Manager supports the following as identity sources:
- LDAP directory servers, either Active Directory, Sun Java System Directory Server, Oracle Directory Server, or OpenLDAP.
- Active Directory Global Catalogs, when some or all of the Active Directory servers in its Active Directory forest are used as identity sources. In such a case, the Global Catalog is used for runtime activities, for example, looking up and authenticating users, and resolving group membership within the Active Directory forest. The Global Catalog cannot be used to perform administrative functions.
- The Authentication Manager internal database, used for administrative operations, such as enabling users for on-demand authentication and risk-based authentication.
- RSA Authentication Agents: An authentication agent is a software application installed on a machine, such as a domain server, web server, or personal computer, that enables authentication. The authentication agent is the component on the protected resource that communicates with RSA Authentication Manager to process authentication requests. Any resource that is used with SecurID authentication, on-demand authentication (ODA) or risk-based authentication (RBA) requires an authentication agent.
-
Risk-Based Authentication for a Web-Based Resource: Risk-based authentication (RBA) protects access to web-based resources and applications. Deploying RBA requires integrating the resource with Authentication Manager. Authentication Manager provides a template to facilitate the integration process. Once integrated, the web-based resource automatically redirects users to Authentication Manager, which does either of the following:
- Authenticates the user and returns proof of authentication to the resource
- When the risk level is high, prompts the user to provide further credentials, such as the correct answers to pre-configured security questions, before returning proof of authentication.
The web-based resource presents the proof of authentication to Authentication Managerfor verification and allows the user access to the resource.
- RSA RADIUS Overview: You can use RSA RADIUS with RSA Authentication Manager to directly authenticate users attempting to access network resources through RADIUS-enabled devices.
- Web Tier: A web tier is a lightweight application server that hosts several Authentication Manager services securely in the network DMZ. Services such as risk-based authentication (RBA), the Cryptographic Token Key Initialization Protocol (CT-KIP) for the dynamic provisioning of software tokens, and the Self-Service Console may be required by users outside of your corporate network. If your network has a DMZ, you can use a web tier to deploy these services in the DMZ.
- Self Service: Self-Service is a web-based workflow system that provides user self-service options and automates the token deployment process.
- Load Balancer: If your deployment includes more than one web tier, you can add a third-party load balancer. The web-tier deployment can be used with a load balancer or you can use round robin DNS.
Owing to its ability to be deployed easily in an environment and provide multi-factor authentication with ease, the RSA Authentication Manager is preferred across most mission critical environments. A second’s non-availability of the authentication manager, an overload condition or authentication failure, ineffective caches of the RSA Authentication Manager, and intense response time during authentication process can cause serious harm to not only the performance of the RSA Authentication Manager, but also the services that rely on it. Continuous monitoring of the RSA Authentication Manager and prompt detection and resolution of anomalies is hence imperative. For continuously monitoring the RSA Authentication Manager, the eG Enterprise provides a specialized monitoring model, which is explained in the upcoming topics.